Cryptology vs Cryptography vs Cryptanalysis: What is the difference?
Let’s discuss Cryptology vs Cryptography vs Cryptanalysis.
Table: Cryptography vs Cryptanalysis vs Cryptology
| Aspect | Cryptography | Cryptanalysis | Cryptology |
|---|---|---|---|
| Definition | The art and science of securing information through encryption and decryption techniques. | The study of breaking encrypted codes and deciphering messages without possessing the decryption key. | The broader field that encompasses both cryptography and cryptanalysis. |
| Focus | Creating secure systems and designing algorithms to protect data during transmission and storage. | Analyzing ciphertexts, identifying patterns, and exploiting vulnerabilities to crack codes. | Investigating all aspects of secure communication, including both creating and breaking systems. |
| Purpose | To ensure confidentiality, integrity, and authenticity of information. | To reveal weaknesses in cryptographic algorithms and improve their security. | To safeguard digital secrets and maintain a delicate balance between secrecy and decryption. |
| Analogy | The shield that protects information. | The sword that pierces through cryptographic defenses. | The battlefield where both sides clash—creation and decryption. |
Remember, while cryptography builds the fortress, cryptanalysis seeks the chinks in its armor, and cryptology oversees the entire battlefield. 🗝️🔒
Introduction
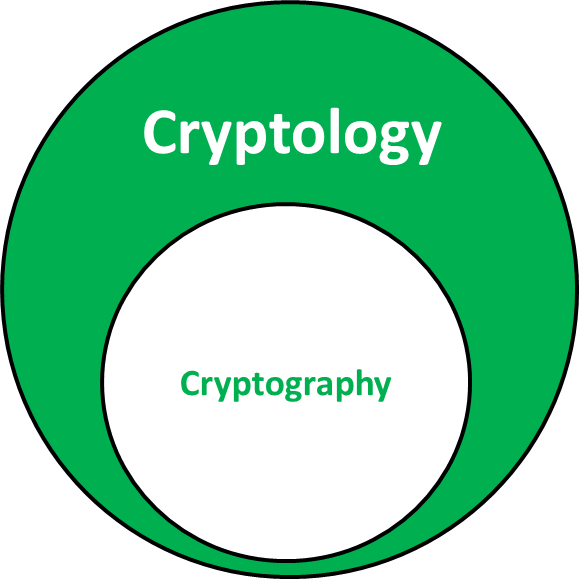
Cryptology, a captivating blend of mathematics, computer science, and secrecy, encompasses the study of secure communication. It encompasses both the art of creating unbreakable codes and the science of breaking existing ones. In this article, we’ll delve into the intricacies of cryptology, focusing on three key aspects: cryptography, cryptanalysis, and the broader field of cryptology itself.
Imagine a world where messages could be transmitted without fear of interception, where confidential data remained impervious to prying eyes. Cryptology aims to make this vision a reality. So, let’s begin our exploration by understanding the fundamental components of this fascinating domain.
Stay with us as we demystify cryptology, decipher the nuances of cryptography, and explore the art of cryptanalysis. By the end of this article, you’ll not only grasp the differences between these terms but also appreciate their impact on our digital security landscape.
Next up, let’s dive into the heart of cryptology: What is Cryptography?
What is Cryptography?
Cryptography, often referred to as the guardian of secrets, lies at the heart of secure communication. It’s the art and science of transforming information into a format that is indecipherable to unauthorized parties. Let’s break down the key aspects of cryptography:
- Encryption and Decryption:
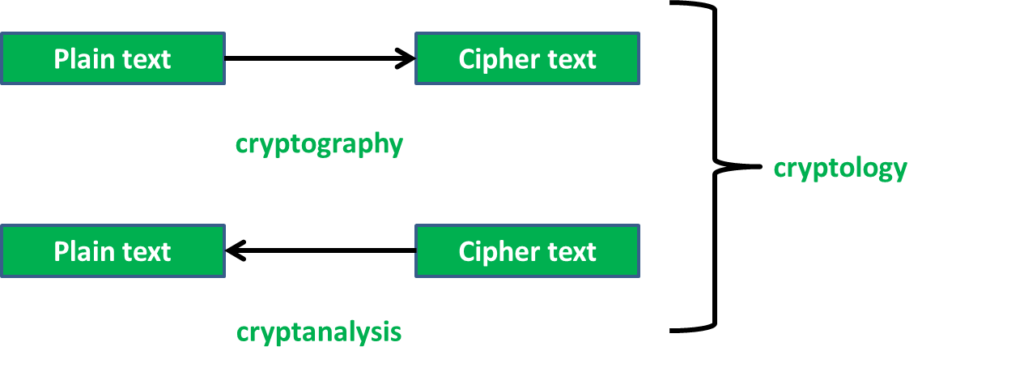
- At its core, cryptography involves two fundamental operations: encryption and decryption.
- Encryption: This process converts plaintext (readable data) into ciphertext (encoded data) using a cryptographic algorithm and a secret key. The resulting ciphertext appears as gibberish to anyone without the corresponding key.
- Decryption: The reverse operation, decryption, transforms ciphertext back into plaintext using the same key.
- Example: When you log in to your online banking portal, your password is encrypted during transmission to prevent eavesdropping.
- Types of Cryptographic Algorithms:
- Cryptographic algorithms come in various flavors, each with specific use cases:
- Symmetric-key algorithms: These use a single secret key for both encryption and decryption. Examples include the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES).
- Asymmetric-key algorithms: These involve a pair of keys: a public key for encryption and a private key for decryption. RSA and Elliptic Curve Cryptography (ECC) fall into this category.
- Hash functions: These produce fixed-length hash values (digests) from input data. Hashes are used for data integrity verification and password storage.
- Stream ciphers and block ciphers: These determine how data is processed during encryption.
- Choosing the right algorithm depends on factors like security requirements, computational efficiency, and key management.
- Cryptographic algorithms come in various flavors, each with specific use cases:
- Applications of Cryptography:
- Cryptography plays a pivotal role in various domains:
- Secure communication: Encrypting emails, instant messages, and web traffic.
- Data protection: Safeguarding sensitive files and databases.
- Digital signatures: Ensuring the authenticity and integrity of messages.
- Virtual private networks (VPNs): Creating secure tunnels for remote access.
- Blockchain technology: Securing transactions and maintaining trust in decentralized systems.
- Cryptography plays a pivotal role in various domains:
- Real-World Example:
- Imagine Alice wants to send a confidential message to Bob. She encrypts the message using Bob’s public key (asymmetric encryption). Only Bob, with his private key, can decrypt and read the message.
- This process ensures privacy and prevents unauthorized interception.
In summary, cryptography empowers us to communicate securely, protect our data, and maintain trust in an increasingly interconnected world. Now that we’ve explored the basics of cryptography, let’s move on to the broader field of cryptology and unravel its mysteries.
What is Cryptology?
Cryptology, the intricate dance between secrecy and revelation, extends beyond the boundaries of cryptography. Let’s explore this multifaceted field:
- The Holistic View:
- Cryptology encompasses both cryptography and cryptanalysis.
- While cryptography focuses on creating secure communication channels, cryptanalysis aims to break those channels.
- Think of cryptology as the umbrella term that shelters these two contrasting endeavors.
- The Cryptologist’s Playground:
- Cryptologists are the architects of secrecy. They design, analyze, and improve cryptographic systems.
- Their work involves:
- Algorithm Design: Creating robust encryption methods.
- Key Management: Safeguarding keys and ensuring their distribution.
- Security Protocols: Crafting secure communication protocols.
- Cryptographic Attacks: Investigating vulnerabilities and devising countermeasures.
- Cryptology in History:
- Throughout history, cryptology played pivotal roles:
- World War II: The Enigma machine and the codebreakers at Bletchley Park.
- Cold War: Espionage, secret codes, and the race for cryptographic supremacy.
- Modern Era: Secure online transactions, digital signatures, and privacy-enhancing technologies.
- Throughout history, cryptology played pivotal roles:
- Real-World Example:
- Imagine a cryptologist analyzing a newly proposed encryption algorithm. They scrutinize its mathematical properties, assess its resistance to attacks, and validate its security guarantees.
- Their goal? To ensure that the algorithm withstands the relentless scrutiny of cryptanalysts.
- Cryptology Beyond Encryption:
- Cryptology extends beyond secrecy:
- Steganography: Concealing information within other data (e.g., hiding a message in an image).
- Quantum Cryptography: Leveraging quantum principles for unbreakable communication.
- Side-Channel Attacks: Exploiting unintended information leaks (e.g., timing or power consumption).
- Cryptology extends beyond secrecy:
In summary, cryptology is the symphony where cryptography and cryptanalysis harmonize. It fuels our quest for secure communication while challenging us to stay one step ahead of adversaries.
What is Cryptanalysis?
Cryptanalysis, the art of unraveling secrets, takes center stage in our cryptological journey. Let’s delve into its depths:
- The Puzzle Solvers:
- Cryptanalysts are the detectives of the cryptological world.
- Their mission? To crack the codes, decipher the ciphers, and reveal hidden messages.
- They employ a mix of intuition, mathematics, and sheer persistence.
- Breaking the Code:
- Cryptanalysis involves:
- Frequency Analysis: Studying the occurrence patterns of letters or symbols in ciphertext.
- Known-plaintext Attacks: Leveraging known plaintext-ciphertext pairs to deduce the encryption key.
- Brute Force: Exhaustively trying all possible keys.
- Side Channels: Exploiting unintended information leaks (e.g., timing, power consumption).
- Example: Alan Turing’s team breaking the German Enigma code during World War II.
- Cryptanalysis involves:
- Types of Cryptanalysis:
- Ciphertext-only attack: The cryptanalyst has only the encrypted message.
- Known-plaintext attack: Some plaintext-ciphertext pairs are known.
- Chosen-plaintext attack: The cryptanalyst can choose specific plaintexts to encrypt.
- Adaptive chosen-plaintext attack: Adjusting the chosen plaintexts based on previous results.
- Differential cryptanalysis: Analyzing differences between pairs of plaintexts and corresponding ciphertexts.
- Cryptanalysis in History:
- Iconic moments:
- Breaking the Enigma: Turing’s team at Bletchley Park.
- Zimmermann Telegram: Intercepted during World War I.
- Modern Challenges: Cracking encrypted communications in the digital age.
- Iconic moments:
- Real-World Example:
- Imagine a cryptanalyst analyzing intercepted encrypted emails. They look for patterns, anomalies, and clues.
- Their goal? To uncover the hidden message and thwart malicious intent.
- Cryptanalysis vs. Cryptography:
- While cryptographers build the locks, cryptanalysts pick them.
- It’s a perpetual cat-and-mouse game: as encryption methods evolve, so do the techniques to break them.
In summary, cryptanalysis fuels innovation by exposing vulnerabilities. It keeps cryptographers on their toes, ensuring that our secrets remain truly secure. now let’s talk about Cryptology vs Cryptography.
Cryptology vs Cryptography
Let’s unravel the intricate dance between cryptology and cryptography. While these terms are closely related, they serve distinct purposes:
- Cryptography:
- Definition: Cryptography involves the art and science of transforming information into an unintelligible format using mathematical algorithms.
- Purpose: Its primary goal is to ensure secure communication by encrypting data.
- Example: When you send a confidential email, cryptography ensures that only the intended recipient can decipher the message using the correct decryption key.
- Cryptology:
- Definition: Cryptology is the broader field that encompasses both cryptography and cryptanalysis.
- Scope: It goes beyond encryption and decryption, diving into the theoretical and mathematical aspects of information security.
- Researchers and Practitioners: Cryptologists explore new encryption methods, analyze existing systems, and study the underlying principles.
- Example: A cryptologist might investigate the mathematical properties of a proposed encryption algorithm to assess its security.
- Cryptology in Action:
- Imagine cryptology as a toolbox:
- Cryptography provides the locks (encryption) and keys (decryption).
- Cryptanalysis tests those locks, attempting to pick them open.
- Together, they form a dynamic duo, ensuring that our secrets remain safe yet challengingly breakable.
- Imagine cryptology as a toolbox:
- Real-World Scenario:
- Suppose a cryptologist designs a novel encryption algorithm. They rigorously analyze its mathematical properties, evaluate its resistance to attacks, and publish their findings.
- Meanwhile, cryptanalysts examine the algorithm, attempting to find weaknesses or vulnerabilities.
- This collaborative dance drives innovation and keeps our digital world secure.
In summary, while cryptography secures our messages, cryptology fuels our understanding of how encryption works and how it can be improved. As we move toward the conclusion, let’s address some common questions about these fascinating fields. Now that we’ve explored the intricacies of cryptanalysis, let’s step back and compare the trio: cryptology, cryptography, and cryptanalysis.
Difference between Cryptography, Cryptanalysis, and Cryptology
Let’s dissect the intricacies of these three interrelated fields: cryptography, cryptanalysis, and cryptology. Each plays a distinct role in the world of secure communication:
- Cryptography:
- Purpose: Cryptography focuses on creating secure communication channels.
- What It Does:
- Develops encryption algorithms and protocols.
- Safeguards data during transmission.
- Enables secure messaging, file transfer, and digital signatures.
- Example: When you make an online purchase, cryptography ensures that your credit card details remain confidential during the transaction.
- Cryptanalysis:
- Purpose: Cryptanalysis aims to break existing encryption methods.
- What It Involves:
- Analyzing cryptographic systems to find vulnerabilities.
- Investigating ciphertext patterns and mathematical properties.
- Breaking codes and deciphering messages.
- Example: A cryptanalyst might crack an encrypted email to reveal its original content.
- Cryptology:
- Definition: Cryptology is the broader field that encompasses both cryptography and cryptanalysis.
- Scope:
- Studies the theoretical and mathematical aspects of information security.
- Explores encryption, decryption, and their underlying principles.
- Researchers and Practitioners:
- Cryptologists delve into algorithm design, key management, and security protocols.
- They bridge the gap between theory and practical implementation.
- Example: Cryptologists analyze proposed encryption algorithms, ensuring their robustness and resistance to attacks.
In summary, cryptography builds the locks, cryptanalysis tests them, and cryptology provides the overarching framework. Together, they form the backbone of secure communication. As we conclude our exploration, remember that understanding these concepts empowers us to navigate the digital landscape with confidence. 📜🔒
FAQs
Let’s address some common questions related to cryptology, cryptography, and cryptanalysis:
Is cryptography a branch of cryptology?
- Yes, cryptography is a subset of cryptology. Cryptology encompasses both encryption and decryption techniques, while cryptography specifically deals with secure communication methods.
What is the difference between cryptosystem and cryptography?
- A cryptosystem refers to the entire system of encryption and decryption, including algorithms, keys, and protocols. Cryptography, on the other hand, focuses specifically on the techniques used for secure communication.
Is it cryptologist or cryptanalyst?
- Both terms are used interchangeably, but there’s a subtle distinction:
- A cryptologist studies cryptology as a whole, including both cryptography and cryptanalysis.
- A cryptanalyst specifically focuses on breaking encryption methods.
Is it cryptology or cryptography?
- Cryptology is the umbrella term that covers both cryptography and cryptanalysis. While cryptography deals with secure communication, cryptology extends beyond encryption to include decryption and related research.
What is cryptography cryptanalysis?
- Cryptanalysis involves analyzing and breaking existing encryption methods. Cryptanalysts study ciphertext patterns, mathematical properties, and vulnerabilities in cryptographic systems.
In conclusion, understanding these terms empowers us to navigate the intricate world of secure communication. Whether you’re a curious learner or a seasoned professional, cryptology continues to shape our digital landscape. 🗝️🔍
Conclusion
In our journey through the fascinating world of cryptology, we’ve explored the intricate dance between cryptography, cryptanalysis, and the broader field of cryptology itself. Let’s recap our discoveries:
- Cryptography:
- It’s the art and science of transforming information into an unintelligible format.
- Encryption and decryption form its core operations.
- From secure messaging to digital signatures, cryptography safeguards our digital interactions.
- Cryptanalysis:
- The cryptanalysts’ mission is to break existing encryption methods.
- They employ frequency analysis, known-plaintext attacks, and other techniques.
- Iconic moments like breaking the Enigma code highlight their pivotal role in history.
- Cryptology:
- Cryptology is the symphony where cryptography and cryptanalysis harmonize.
- It extends beyond secrecy, exploring steganography, quantum cryptography, and more.
- Cryptologists bridge theory and practice, ensuring our security remains robust.
As we conclude, remember that understanding these concepts empowers us to navigate the digital landscape with confidence. Whether you’re a curious learner, a security enthusiast, or a future cryptologist, keep exploring, questioning, and innovating. Our secrets remain safe because of the tireless efforts of those who build, test, and protect our cryptographic systems.
So next time you send a secure message, appreciate the intricate dance of cryptology—the silent guardian of our digital secrets. 🗝️🌐🔒
Learn More Here